This a saga article documenting my preparation to become AWS Associate Architect Certified.
I work for many years with AWS services, but I want to define and improve my knowledge and so I am preparing for the exam. For all people who want to become certified or study more AWS’s contents, you are in the right place!
As an AWS Associate Architect, you should be familiar with the security concerns surrounding AWS Identity and Access Management (IAM).
IAM: Access managament on AWS
IAM is the acronym of Identity and Access Management, Global Service and it’s a crucial component of AWS security, as it determines who has access to your AWS resources and what actions they can perform.
You can create groups and assign IAM policies to the groups. This allows you to manage the permissions for multiple IAM users as a single unit, rather than managing permissions for each individual user. Once you have created a group, you can add IAM users to the group, and the group members will inherit the permissions assigned to the group.
This makes it easier to manage the permissions of multiple IAM users, as you can make changes to the group policy and have those changes apply to all members of the group.
Remember groups can’t contain groups but only users.
You can assign policies to IAM users or groups in the following steps:
- Create an IAM policy: An IAM policy is a document that specifies the permissions for an AWS resource. You can create an IAM policy using the AWS Management Console, AWS CLI, or AWS SDKs.
- Attach the policy to a user or group: Once you have created an IAM policy, you can attach it to an IAM user or group. To attach the policy to a user, go to the IAM console, select the user, and then choose the “Add inline policy” option. To attach the policy to a group, go to the IAM console, select the group, and then choose the “Add policy” option.
When assigning policies to IAM users or groups, it is important to implement the following principles:
- Least privilege: Grant only the permissions that are necessary to perform a specific task.
- Separation of duties: Divide responsibilities among multiple users to ensure that no single user has too much power.
- Role-based access control: Assign permissions based on the role of the user, rather than the identity of the user.
- Monitoring and auditing: Regularly monitor IAM activity and audit the policies to ensure that they are still effective and secure.
An AWS IAM policy is a document that defines permissions for AWS resources. It is written in JSON and consists of:
- Version: The policy language version being used.
- Statement: An array of one or more policy statements. Each statement specifies the resources, actions, and conditions for which the policy provides or denies permissions.
- Effect: Whether the policy statement is allowing (“Allow”) or denying (“Deny”) access to the resources.
- Principal: Specifies the AWS account or user that the policy statement applies to.
- Action: Specify the AWS service actions that the policy statement allows or denies.
- Resource: Specify the AWS resources that the policy statement applies to.
- Condition: Specifies the conditions under which the policy statement applies. This can include things like the time of day or the location of the request.
What’s EC2 as infrastructure as a Service)?
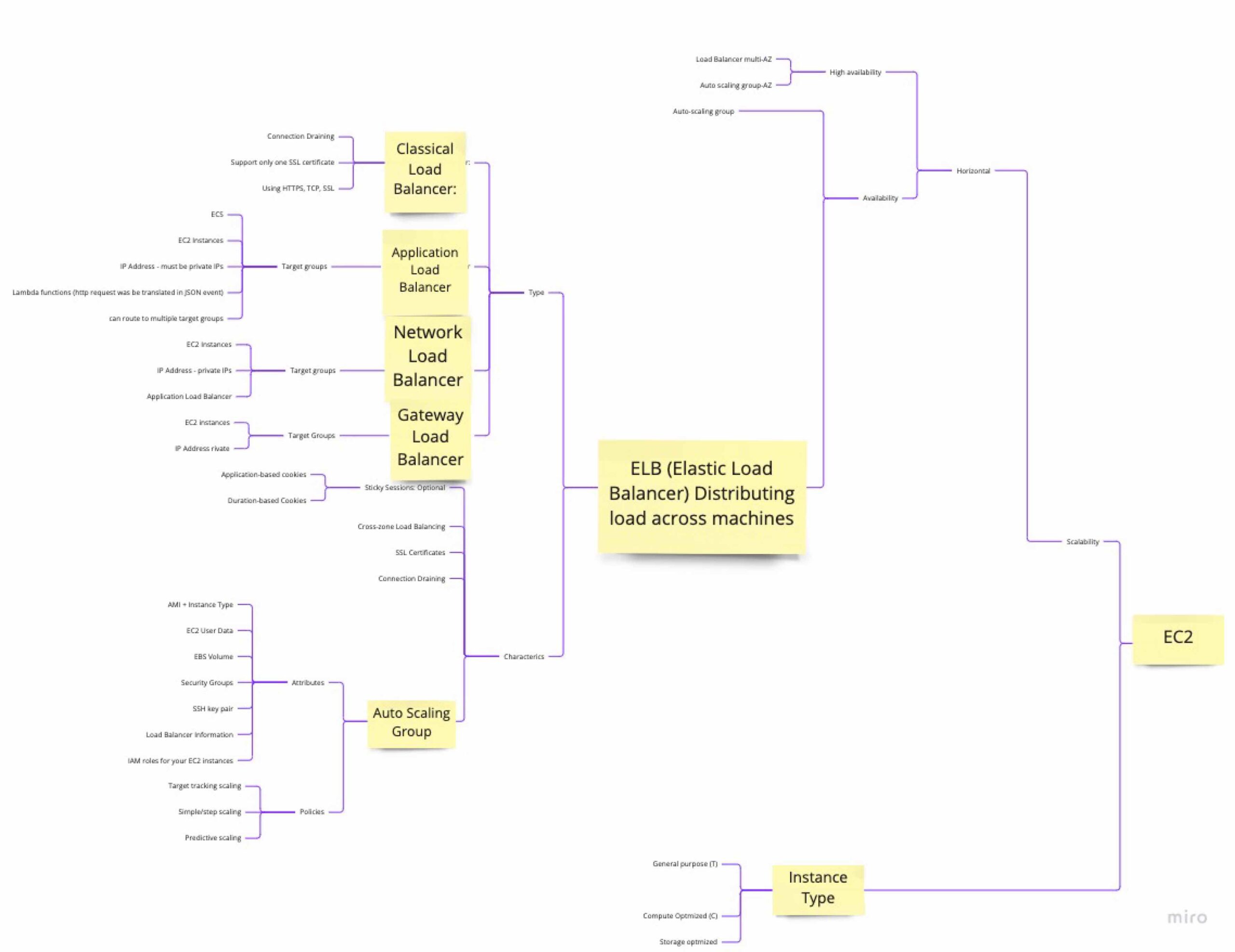
EC2 (Elastic Compute Cloud) is a service provided by Amazon Web Services (AWS) that provides scalable computing capacity in the cloud. It is considered an Infrastructure as a Service (IaaS) solution, as it provides virtualized computing resources over the internet.
With EC2, users can launch virtual machines (called instances) and run their applications on these instances. EC2 allows users to choose from a variety of instance types, operating systems, and software packages to build the environment that best fits their needs. EC2 also provides various tools and features for managing, securing, and scaling instances, making it a flexible and scalable solution for running applications in the cloud.
Users can interact with EC2 instances through APIs, the AWS Management Console, or command-line interfaces such as the AWS CLI. EC2 provides various features for managing and monitoring instances, including automation of common administrative tasks, load balancing, auto-scaling, and security features such as security groups and network access control lists.
Overall, EC2 is a highly scalable, flexible, and secure platform for running a wide range of applications and services in the cloud.
How to create an EC2 instance?
To create an EC2 Instance you must specify the type of instance (who determines CPU, memory, network speed and so on), Key pair type (.pem, ppk) with can log in on ssh, allow SSH traffic from a specific IP or anywhere and choose if allow HTTP traffic from/to the internet or choose storage type and size.
We can set User Data as bootstrapping script the first time you run, as bash script.
If you terminate the instance can be deleted storage is linked as EBS directly depending on how you have configured the instance.
The public IP address changes every time you restart, but the private IP address not changes.
What are instances type EC2?

General purpose instances (for example T2)
EC2 General Purpose Instances are a category of EC2 instances in Amazon Web Services (AWS) that provide a balance of compute, memory, and storage resources for a variety of workloads.
- Cost-effective: instances are generally less expensive than other EC2 instance types, making them a cost-effective option for applications with moderate CPU requirements.
- Balance of CPU and Memory: provide a balance of CPU and memory, making them suitable for a variety of workloads.
- Suitable for a variety of workloads: General Purpose Instances are well-suited for a wide range of applications, including web and application servers, development and test environments, and small to medium databases.
- Enhanced Networking: General Purpose Instances support enhanced networking, which provides higher packet per second (PPS) performance, lower network latency, and lower network jitter.
EC2 Compute Optimized instances (Cx instances)
EC2 Compute Optimized Instances are a category of EC2 instances in Amazon Web Services (AWS) designed for compute-bound workloads that require high CPU performance. The key characteristics of EC2 Compute Optimized Instances include:
- High CPU Performance: Compute Optimized Instances provide a high level of CPU performance, making them ideal for compute-bound workloads such as batch processing, scientific modeling, and web servers serving dynamic content.
- Cost-effective: Compute Optimized Instances are less expensive than other EC2 instance types with a similar level of CPU performance, making them a cost-effective option for compute-bound workloads.
- EBS Optimized Option: Compute Optimized Instances have the option to be EBS optimized, which provides improved network performance for EBS-bound workloads.
- Customizable: Compute Optimized Instances come in multiple sizes with varying amounts of CPU and memory resources, allowing users to select the size that best fits their needs.
- Suitable for a variety of workloads: Compute Optimized Instances are well-suited for a wide range of compute-bound workloads, including batch processing, scientific modeling, and web servers serving dynamic content.
- Enhanced Networking: Compute Optimized Instances support enhanced networking, which provides higher packet per second (PPS) performance, lower network latency, and lower network jitter.
Overall, EC2 Compute Optimized Instances provide high CPU performance and are a cost-effective option for compute-bound workloads. They are suitable for a wide range of applications that require a high level of CPU performance.
Memory Optimized instances
EC2 Memory Optimized Instances are a category of EC2 instances in Amazon Web Services (AWS) designed for memory-intensive workloads that require a high amount of memory. The key characteristics of EC2 Memory Optimized Instances include:
- High Memory: Memory Optimized Instances provide a high amount of memory, making them ideal for memory-intensive workloads such as high-performance databases, distributed caching, and in-memory analytics.
- Cost-effective: Memory Optimized Instances are more expensive than other EC2 instance types with a similar level of CPU performance, but provide a cost-effective option for memory-intensive workloads.
- EBS Optimized Option: Memory Optimized Instances have the option to be EBS optimized, which provides improved network performance for EBS-bound workloads.
- Customizable: Memory Optimized Instances come in multiple sizes with varying amounts of CPU, memory, and storage resources, allowing users to select the size that best fits their needs.
- Enhanced Networking: Memory Optimized Instances support enhanced networking, which provides higher packet per second (PPS) performance, lower network latency, and lower network jitter.
Some examples of Memory Optimized Instances include:
- X1e instances: These instances are optimized for large-scale, enterprise-class, in-memory applications and provide the highest amount of memory and the lowest cost per GiB of RAM.
- R5 instances: These instances are optimized for memory-intensive workloads such as high-performance databases and distributed caching.
- Z1d instances: These instances are optimized for applications requiring high CPU performance and a high amount of memory.
Overall, EC2 Memory Optimized Instances provide a high amount of memory and are a cost-effective option for memory-intensive workloads. They are suitable for a wide range of applications that require a high amount of memory.
EC2 Storage Optimized
EC2 Storage Optimized Instances are a category of EC2 instances in Amazon Web Services (AWS) designed for storage-intensive workloads that require high input/output (I/O) performance and low latency. The key characteristics of EC2 Storage Optimized Instances include:
- High I/O Performance: Storage Optimized Instances provide high I/O performance, making them ideal for storage-intensive workloads such as NoSQL databases, distributed file systems, and data warehousing.
- Cost-effective: Storage Optimized Instances are less expensive than other EC2 instance types with a similar level of I/O performance, making them a cost-effective option for storage-intensive workloads.
- Large Storage: Storage Optimized Instances come with a large amount of local storage, allowing users to store a large amount of data directly on the instance, without the need for additional storage.
- Suitable for a variety of workloads: Storage Optimized Instances are well-suited for a wide range of storage-intensive workloads, including NoSQL databases, distributed file systems, and data warehousing.
Examples of EC2 Storage Optimized Instances include:
-
- d2 instances, which are designed for dense storage and high sequential read and write performance.
- i3 instances, which are designed for high I/O performance and low latency.
- h1 instances, which are designed for big data and data warehousing workloads.
How to bootstrap scripts on Ec2 Instance?
EC2 user data is data that can be passed to an EC2 instance at launch time. It is used to configure the instance and perform tasks such as installing packages, writing files, or otherwise modifying the instance. The user data is passed to the instance as a script and can be encoded in either plain text or base64. User data can be up to 16 KB in size.
AWS EC2 instances use this user data to run custom scripts or provide configuration information when they launch. This is particularly useful for automating the process of setting up and configuring instances, as it allows you to specify all of the necessary information in a single location, rather than having to manually configure each instance after it is launched.